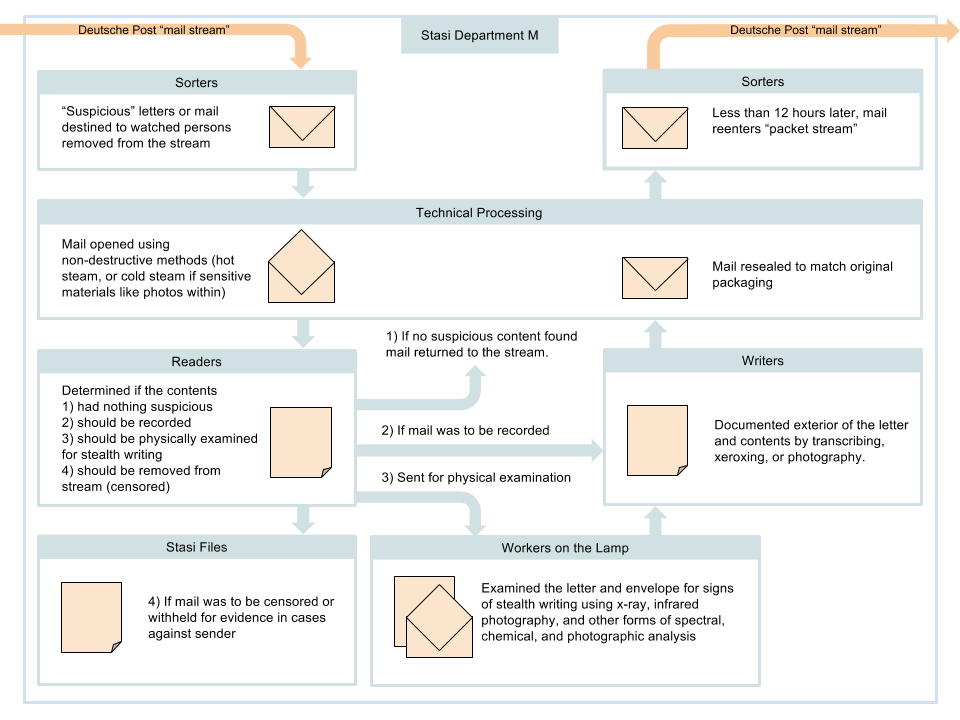
The number of cards in the Stasi indexes grew to an incredible 39,000,000 by 1989. In order to provide constant access to this massive material data system they created various special storage units and containers as it expanded. The current mechanical powered card indexes in place at the BTsU were found after the end of the GDR and are still in use in order to meet requests of citizens who wish to view the data the Stasi kept on them.

Mechanical index card file organization system used by the Stasi.
Beginning in the 1960s, the MfS also used various electronic databases to track citizens.* These databases were never fully implemented as a primary source of storage because computing and software available in the GDR at the time, even machines stolen or purchased in the west, were unreliable. For six years the Stasi mirrored essential data from the F16 personal card into an electronic format. In 1975, Department XII, responsible for central data collection, information and storage, introduced the “System of automatic pre-selection” (SAVO) which allowed workers to verify that a person was “not yet recorded” in the system. This considerably reduced the time it took for verification, however it still required a substantial 12–21 days for a process to complete.
By 1986 SAVO 2.0 was introduced providing printing functionality, increased capacity—now containing all data from the F16 card—and reducing search times to 1–6 days. It also provided teletype connections eliminating the need for couriers and allowing multiple agencies (passport control, tourism, etc.) to use the same data source simultaneously. (The Key to Power, 6) While this greatly modernized the surveillance workflow of the Stasi, it continued to act only as a duplicate of the F16 card, which was still faster for priority inquiries, and less susceptible to errors.

A computer used by the Stasi. Source: BBC
The logic for these implementations is echoed in modern database planning and use. While redundancy is employed for backups and increasing access speed across global networks, there is still a “master” copy of all data, or in the case of distributed system, automated processes (software) that merge and maintain distributed data into a master. Like the Stasi’s decision to completely mirror portions of the F16 system, modern systems use whichever implementation is most reliable for the master, while summarizations of that data may be “pushed” to other indexes for faster retrieval.
The Stasi’s use of multiple systems, as well as the F16 and F22 card also preempt the concept of “joins”, which is a powerful feature in relational database management systems (RDBMS), to allow various pieces of data to be spread out across multiple indexes. Like the registration number on the F16/22 cards, records from multiple discrete RDBMS can be “joined” by matching a single identification field in order to supply additional, or limit access to other data, when performing queries.
Multiple other computerized database systems were developed or used by the Stasi, including SOUD, a collection of information on the “enemy” shared between the GDR, Bulgaria, Cuba, Poland, the USSR, Czechoslovakia, Hungary, and Vietnam. The most expansive of all their electronic indexes, was the central database of personal data (ZPDB). Introduced in 1981, by the end it contained records on over 1,320,000 people, 417,000 situations, 558,000 objects, and numerous related information.
The desire to track not just people, but occurrences and objects is directly visible in the largest person tracking organization today. In Facebook’s “Social Graph”, introduced in 2007, any person, place, thing, event, anything that can be named, is recorded in a massive attempt to commodify everything and our connections to it. Like the Stasi ZPDB, everything in the Facebook Social Graph is indexed by a unique identification string as single record, which Facebook considers a “node,” with links or “edges” that connect them. These definitions are based on Facebook’s desire to do data science on the their information, applying statistics and other mathematical operations from graph theory in order to understand their data and predict (and manipulate) the behavior of users.
*Regrettably, all electronic databases and their magnetic storage was destroyed not long after the end of the GDR. Meaning, BStU staff now use the original paper F16 card system to provide services to the public.
- The key to power: Card indexes and other finding aids practices of State Security. Archivar 64. Jahrgang Heft 04 November 2011.